Our Business
- Corporate Outline
- Security Business
- System Integration Services Business
This introduces "Security" and "SI Services," the two businesses that comprise the segment, and their sales composition.
Outline of operations
LAC provides security solution services, an area it pioneered in the industry, and a wide range of SI services as an independent IT vendor, and we have a solid customer base consisting mainly of large corporations.
With a team of security engineers boasting some of the highest levels of knowledge in Japan, we protect our clients from the threat of malicious and increasingly sophisticated cyber-attacks. Supported by the SI business, which has a stable revenue base, we aim for company growth based on our security business, where we have a competitive advantage in the market.
Business segment
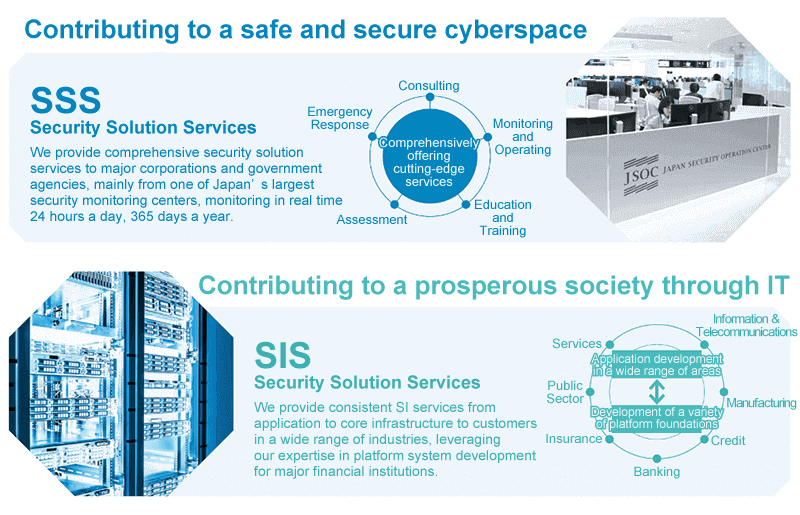
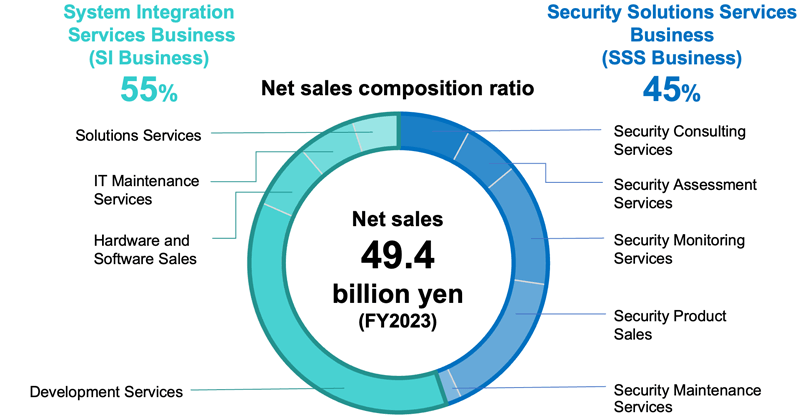
LAC's business segments are comprised of the Security Solution Services (SSS) business and the System Integration Services (SIS) business.
Within the business segments, there are five sub-segments for the SSS business and four sub-segments for the SIS business. The core SSS businesses are "Consulting Services", "Assessment Services", and "Monitoring Services", and the core SIS business is "Development Services." In addition, "product sales" and "maintenance services" for each business, and "Solutions Services" for the SIS business are mainly the businesses of purchasing and selling products and solutions from other companies, and they are positioned to complement the core Services businesses.
Here we provide an overview of the key characteristics and services of LAC's security business as well as the business performance of the SSS Business Division, which constitutes a reportable segment.
- Business Characteristics
- Principal Services
- Overview of Business Sales Composition of the SSS Business Division
Business Characteristics
Provision of specialized services by security engineers
LAC's security business involves the provision of specialized services by security engineers, not the sale of security solutions products, such as anti-virus software or security devices. The cornerstone of LAC's competitive strength is service capabilities made possible by our engineers' skills underpinned by highly advanced knowledge and expertise.
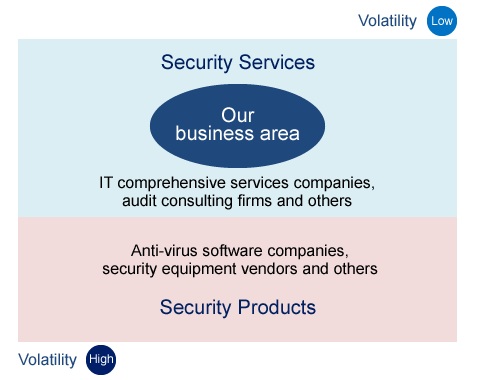
Provision of advanced, high-quality services to large corporations and other customers
LAC provides advanced, high-quality services to major corporations and government agencies. We serve corporate customers in wide-ranging fields, notably financial services and e-commerce, as well as the telecommunications, services, and manufacturing industries. The principal services are as follows.
Principal services
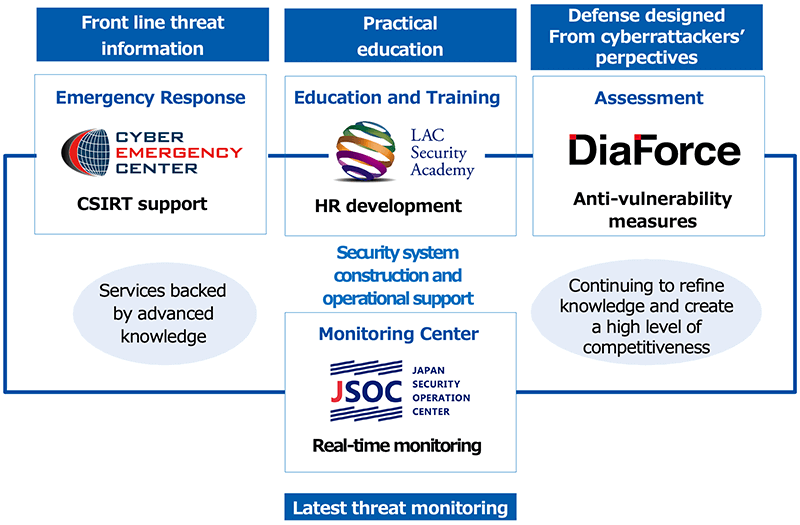
- Consulting services
Security system construction and operational support, including emergency response services, and support for education and training - Assessment services
Assessment of security vulnerabilities of websites, servers, etc. - Monitoring services
Real-time monitoring of customers' networks 24 hours a day, 365 days a year by expert analysts - Product sales and maintenance
Sourcing, sale, and maintenance of security solutions products necessary for monitoring services
In particular, the monitoring services provided by the Japan Security Operation Center (JSOC®), one of the largest security monitoring centers in Japan, constitute LAC's core security business, which generates recurring income and stable profits. We also provide advanced on-site services underpinned by up-to-date cyberattack information and a wealth of knowledge about security-related matters, such as the effectiveness of different security solutions. The JSOC services include the Cyber 119 emergency response service, under which experts rush to the customer's premises when a cyberattack incident has occurred, and an assessment service for investigating vulnerabilities of websites and servers, which was the forerunner of LAC's cyber-security business.
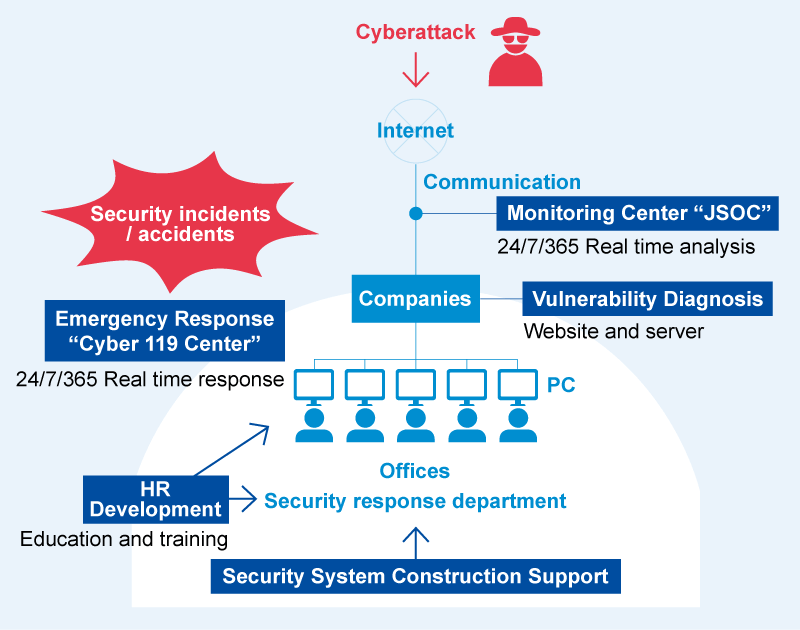
The source of LAC's competitive strength is the ability to utilize such up-to-date security solutions intelligence obtained from threat information independently gathered in the field. This intelligence enables us to provide customers with more practical security services.
Over the course of some 30 years in business, LAC has worked to raise awareness of the need for security solutions. During that time, we have provided cybersecurity services to companies and organizations on more than 36,000 occasions in total.
| Services | Cumulative number of installations at companies and government offices |
|---|---|
| Security Assessment | 27,500 times |
| Consulting Services | 3,650 times |
| Emergency Response | 4,800 times |
| Services | Number of installations at companies and government offices |
|---|---|
| Security Monitoring | About 1,000 companies/organizations |
(As of April, 2024)
Principal Services
Security Monitoring Services
JSOC: One of Japan's largest security monitoring centers
The central hub of LAC's monitoring services is the Japan Security Operation Center (JSOC), one of the largest security monitoring centers in Japan. The forerunner of JSOC was a security monitoring center set up in 2000 in the Odaiba district of Tokyo to assist in monitoring the official website of the Kyushu-Okinawa G8 Summit and responding to any intrusions. The original JSOC opened in Tokyo's Toranomon district in 2002 and was relocated to the Hirakawacho district in June 2010. It underwent a major refurbishment in July 2017 in response to expanding demand and to enhance the workplace environment.
Before

After

LAC Falcon®: LAC's independently developed monitoring and operational support system
One mechanism that supports JSOC is LAC Falcon, an analysis engine developed in-house. The engine narrows down an enormous number of logs (data processing records) of what appear to be cyberattacks, identifying 15,000 to 20,000 high-risk incidents from among more than 2.5 billion logs per day. Security analysts familiar with all security equipment and well-versed in cyberattack techniques and methods of defending against such attacks perform real-time monitoring and analysis 24 hours a day, 365 days a year.
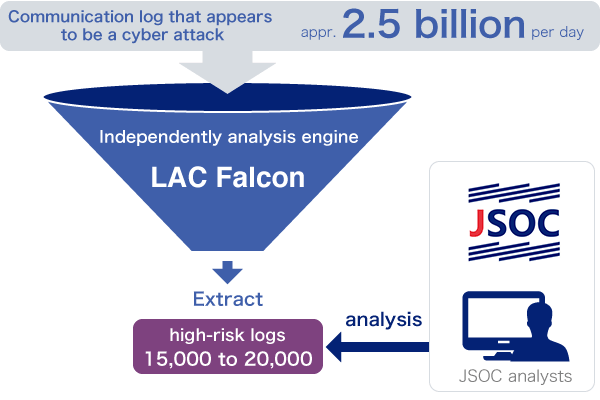
This system, developed in-house in 2012, made it possible to substantially shorten the time required--previously several months--to facilitate the smooth adoption of security solutions products, many of which are produced outside Japan. The superiority of LAC Falcon lies in the ability to facilitate rapid adoption of highly effective security solutions products that dominate the market globally. Another feature of the system is multi-vendor support.
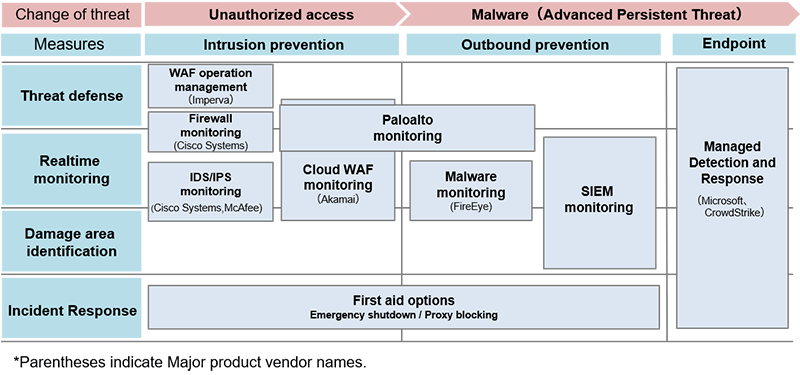
Furthermore, LAC provides a managed security service (MSS), performing security functions on behalf of users. These functions include fraud detection capability performance management, event detection, policy management, log management, and management and operation of security monitoring equipment in accordance with the manner in which user's utilize their networks.
JSIG: LAC's proprietary detection rules
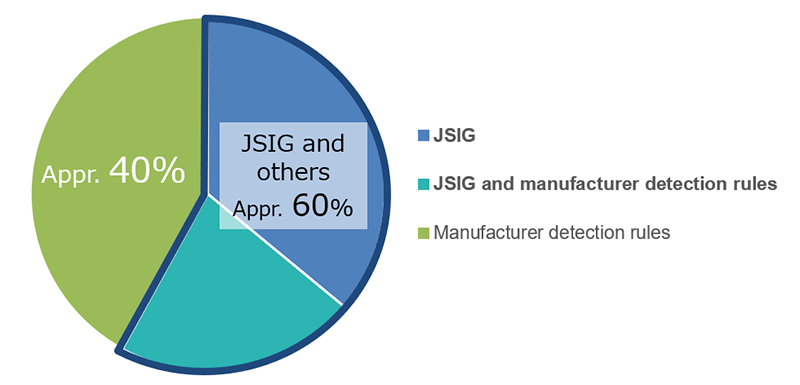
Another characteristic of LAC's monitoring services is JSIG, our proprietary detection rules (in the form of a so-called "patch") provided for use with monitoring equipment. Using JSIG, we respond to threats specific to Japan that are difficult to detect with the standard features of security products, many of which come from overseas. The use of JSIG in conjunction with up-to-date threat information accumulated in daily security monitoring accounts for some 60% of all detected critical incidents. Having such proprietary detection rules is another differentiating factor that sets LAC apart from competitors.
Emergency Response Services
Cyber Emergency Center®: Staffed by experts specializing in incident response
Cyber 119 is an emergency response service for rapidly assisting customers when a security-related emergency occurs. The service is provided by the Cyber Emergency Center, an organization staffed with experts with professional expertise and track records in successfully responding to numerous incidents.
The center provides a response 24 hours a day, 365 days a year. Services encompass every stage from the initial response/incident response to restoration support, assistance in reinforcing countermeasures (including measures to prevent reoccurrence), and follow up. The ability to obtain information on previously unknown cyberattack techniques and virus samples through frontline response activities helps secure and boost LAC's competitive advantage. The center accepts requests for assistance with incidents from any and all companies, not only existing customers, which is an effective catalyst for starting new business relationships.
Support for in-house CSIRTs that draws on an extensive track record
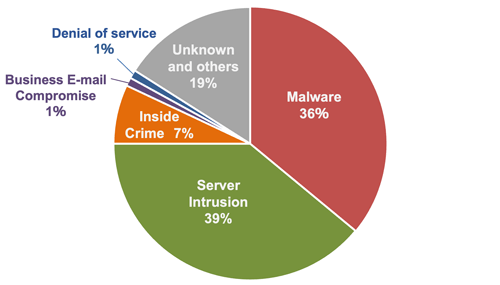
More than ten years have passed since malware (a collective term for malicious code, including viruses, worms, and Trojan horses) began causing damage within company networks. In recent years, the majority of cases handled by the Cyber Emergency Center have been related to malware infections at companies, but recently there has been an increase in server intrusions (as of April 2024).
An example of malware that became famous overnight is the ransomware program Wannacry. It locked victims' computers and demanded payment of a virtual currency ransom in exchange for the unlock password. This cyberattack, which spread around the world, posed a significant risk to company management.
In response to this type of cyber incident, in December 2017 the Ministry of Economy, Trade and Industry formulated and announced the Cybersecurity Management Guidelines Ver.2.0*. Establishment of computer security incident response teams (CSIRT) is a countermeasure mentioned in the guidelines, and the development and operation of CSIRTs has progressed, mainly at large corporations.
* From the perspective of protecting companies from cyberattacks, the Guidelines set out "three principles of cybersecurity management" that corporate managers need to recognize and "ten important items of cybersecurity management" that corporate managers should direct the executives in charge (CISOs, etc.) to observe when implementing information security solutions.
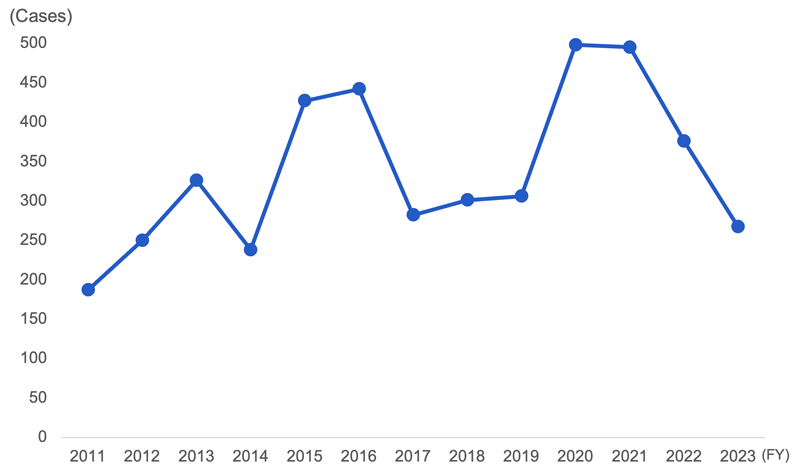
The number of Cyber 119 responses peaked around 2015 (fiscal year 2016 to 2017), when the Japan Pension Service had a data leak incident. The number has since decreased now that large companies have become able to deal with minor incidents in-house thanks to progress with CSIRT formation and operation. However, the number of responses has been on the rise again since 2020, mainly due to the outbreak of malware known as Emotet. As a result, the role of the Cyber Emergency Center is shifting toward dealing with high-level incidents, which are more serious and have a widespread impact.
Rapid response to meet endpoint security requirements
As the practice of taking PCs off company premises to work outside of company networks becomes increasingly widespread, cyberattacks targeting so-called endpoints (terminals), mainly client PCs, are on the rise. Countermeasures that presuppose infection with malware are necessary, and services called endpoint detection and response (EDR) offer a solution for rapidly responding after a malware infection.
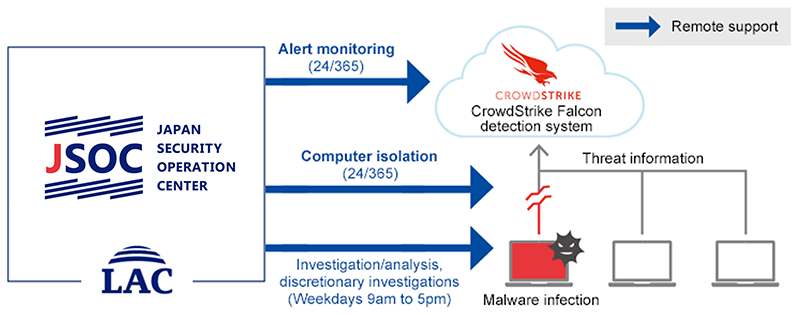
LAC introduced a service that utilizes Microsoft Defender ATP in 2017 and another that utilizes U.S.-based CrowdStrike's highly competitive product platform in 2019. When an infection has been confirmed the Cyber Emergency Center handles computer isolation and investigation and analysis. In this way, we are able to prevent damage from spreading. We expect increasing demand for this service from large corporations that require solutions for their Group companies or supply chains.
Assessment Services
The starting point of the cybersecurity business
LAC began assessment services in 1995 as its first cybersecurity business. Through assessment services, we identify vulnerabilities that increase the risk of cyberattacks and implement cyberattack countermeasures by considering various attacks against customers' IT systems from the perspective of cyberattackers and conducting mock attacks.
Web application assessment: The core assessment business
Web application assessment accounts for a large proportion of LAC's assessment services sales. This is because websites linked to corporate servers are likely to be used as routes of entry for cyberattacks. Due to a sharp rise in website tampering and other cyberattack damage, the need for a service for discovering vulnerabilities in development software used on websites and in web applications is increasing year by year.
A key characteristic of LAC's business is that we don't simply perform assessments using tools provided by vendors. Rather, security engineers known as "white hat hackers" perform advanced assessments utilizing expertise accumulated within LAC over many years. A key feature of our business is that we are able to provide highly advanced assessments by reflecting in the service up-to-date threat information and frontline information obtained from other services.
Extensive service lineup
Against a backdrop of increasingly sophisticated and malicious cyberattacks, we have responded with services focused specifically on measures to counter the expanding malware threat, such as IT security inoculation, involving the provision of training in how to respond to targeted attack emails, and the APT preemptive strike service, which assesses the effectiveness of countermeasures based on the premise of a malware infection within the customer's LAN.
We also provide smartphone application analysis and an IoT security analysis service in accordance with our customers' business environments. Furthermore, we provide the penetration test service, our top-of-the-line service by which we actually penetrate a customer's system through all entry routes and confirm whether data can be obtained for the purpose of verifying the effectiveness of security measures.
At the same time, in view of the increasing speed of service development and provision by customers, we are also providing automated assessment services that achieve high-quality web application assessment in a short time and at a low cost, combining our extensive experience and know-how.
Business seasonality (concentration in the fourth quarter)
Demand for platform assessment, which involves assessing the safety of web applications and servers and network equipment, is concentrated ahead of customers' new service launches beginning in April, and engineer utilization also increases at that time. For this reason, the assessment services business is seasonal, and sales and profit are concentrated in the fourth quarter of the fiscal year. Conversely, demand tends to fall off in the first quarter.
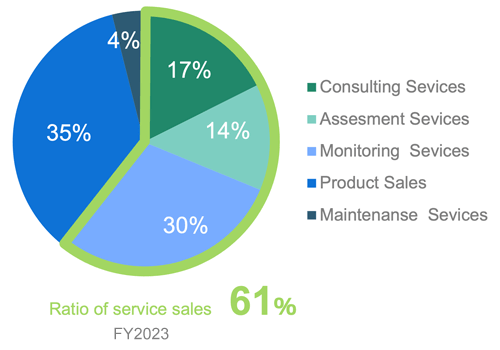
Overview of Business Sales Composition of the SSS Business Division
The core businesses of the SSS Business Division are the service-related businesses: Consulting, assessment, and monitoring and operation. These three businesses accounted for 61% of segment net sales in the year ended March 2024.
Whereas consulting and assessment are businesses in which sales expansion correlates to a degree with workforce expansion, monitoring services are a facilities-based business that generates recurring income and offers the prospect of sales expansion that does not entail substantial personnel increases. However, monitoring services require a certain amount of investment for service expansion and enhancement, and for boosting competitive strength to respond to increasingly sophisticated cyberattacks, such as investment in response to new devices. Our basic policy for this segment is to expand the business by focusing on monitoring services.
Security product sales and security maintenance services are businesses involving the sale and maintenance of equipment sourced from other vendors, mainly devices necessary for monitoring in monitoring services.
Here we provide an overview of the key characteristics and services of LAC's System Integration Services (SIS) business as well as the business performance of the SIS Business Division, which constitutes a reportable segment.
- Business Characteristics
- Principal Services
- Overview of Sales Composition of the SIS Business Division
Business Characteristics
System integration services ranging from infrastructure to applications development
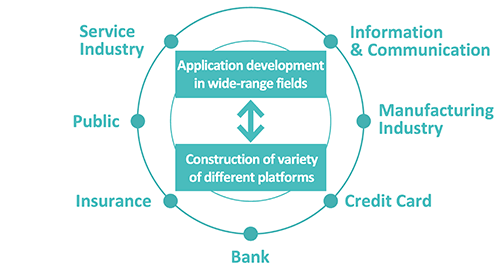
A key characteristic of the System Integration Services business is that LAC is capable of systems development in wide-ranging fields thanks to a background in bank systems development dating back to the company's founding. From mainframes to development of smartphone apps with a focus on web applications, we provide a wide range of platform infrastructure creation and network design and construction services.
A solid business base centered on major corporations
A key strength of LAC is that we have a rock-solid business base centered on major corporations, mainly megabanks and other large banks and major insurance companies. We have expanded our business with enterprise customers as well by providing systems development services associated with customers' server use and development on Linux and other open systems.
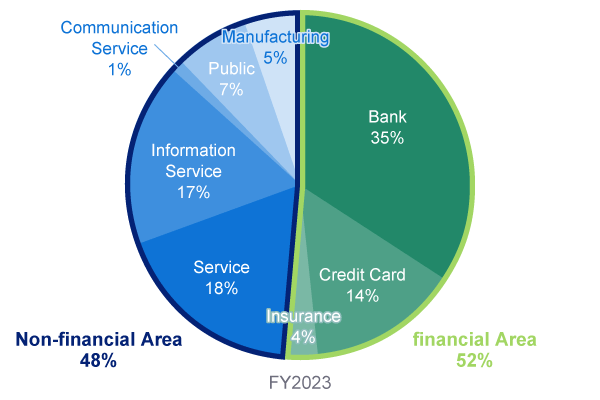
The ratio of sales to the "financial industry" such as banking and credit and "non-financial industry" such as services and information services is roughly half and half, and the number of trading customers is about 230 companies (both as of fiscal year 2023). In addition, about 50-60% of the projects are primary orders, and we are promoting efficient management by utilizing partnerships (outsourcing).
Principal Services
Development Services
End-to-end service provision across all processes
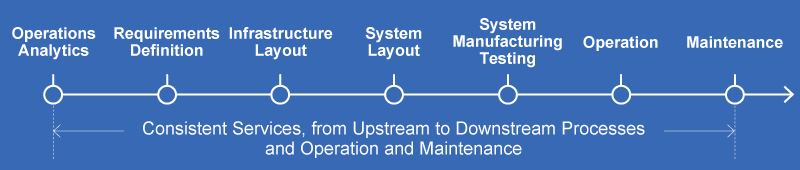
LAC's development services support the development of wide-ranging applications and platform infrastructure construction across all processes, including business process analysis, requirements definition, infrastructure design, system design, system manufacturing testing, operation, and maintenance. Our strength lies in the ability to provide end-to-end services encompassing everything from upstream to downstream processes, operation, and maintenance.
Cloud development
As cloud migration progresses, more and more customers deploy system infrastructure in cloud environments and develop services centered on applications. Since LAC has been involved in development using servers since the second half of the 1990s, mainly for enterprise customers, we have undertaken cloud-related development projects since our customers first began migrating from on-premise to cloud environments.
Because of this background, LAC has undertaken not only applications development, but also construction of public cloud-based infrastructure for AWS, Azure, and IBM Cloud. We are also working on the provision of support for hybrid cloud environments involving the combined use of an on-premise server and a cloud, and multi-cloud environments involving combined use of multiple public clouds.
Cloud migration for the purpose of boosting competitive advantage or efficiency improvement is rapidly expanding even in the financial industry, which had traditionally lacked enthusiasm. LAC has worked since 2018 to develop and strengthen an organizational structure to enable the stable, flexible provision of cloud engineers and is seeing a sharp increase in the number of development projects in today's increasingly expanding cloud environments.
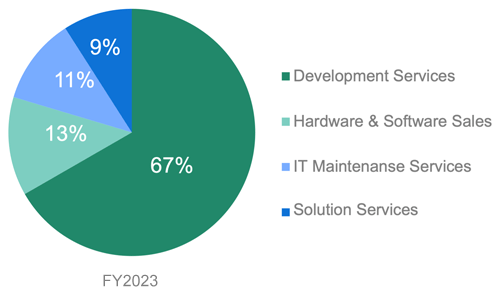
Overview of Sales Composition of the SIS Business Division
Development services that play a key role in systems development are the cornerstone of the SIS Business Division, accounting for 67% of net sales in the fiscal year ended March 31, 2024.
As in the SSS business segment, hardware and software sales and IT maintenance services are businesses involving the sale and maintenance of equipment sourced from other vendors. The scale of the server equipment and network equipment sales business is shrinking due to miniaturization of equipment and other factors. Furthermore, demand is contracting as use of cloud-based servers progresses. Although these are not high-priority businesses, there is a certain level of demand and LAC aims to win orders for update projects.
The Solutions Services segment has provided various solution products that contribute to security measures, including multi-cloud development management tools, for the data center business operated by AXIS Co., Ltd., a subsidiary, and since the fiscal year ended March 31, 2020, for providing customer-problem-solving development services.