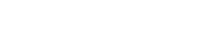How PlugX is related to the APT attack group "DragonOK"
23 JAN 2018 | Warning Alert

Yoshihiro Ishikawa
Our Cyber Emergency Center's threat analysis team has confirmed that there have been several targeted attacks from around Oct. 2017 using *1Poison Ivy's PlugX API Hash code (hereinafter referred to as PIPX) as reported on January 12, 2017 through the JPCERT/CC.
This time, we would like to introduce a group using this malware. We discovered this group of attackers during the course of analyzing the PIPX.
For a description of the detailed functions of PIPX, please refer to the JPCERT analysis as described above.
Common Features of PIPX
Our threat analysis team has confirmed several common features of the PIPX, we would like to explain some of them here.
1. File Information and Execution Method
As shown in Figure 1 and Figure 2, the executable file that drops (installs) PIPX uses a RAR file, in a self-extracting format (SFX) with icon resource information.
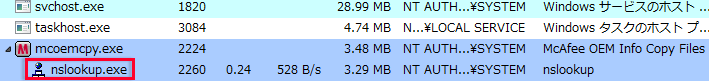
In addition, the executable file is made up of 3 files, and after the DLL side-loading is exploited, the PIPX code is injected into the legitimate process "nslookup.exe" and executed. (Figure 3)
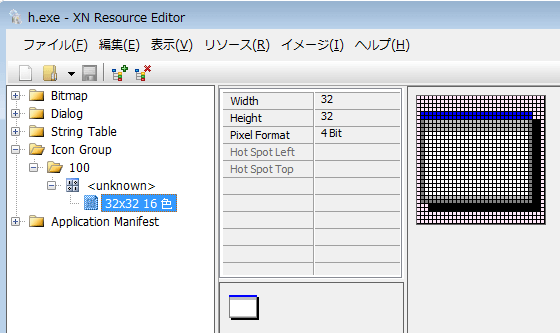
The files included in the PIPX differ slightly depending on the time of the attack. In the campaign we have seen around Oct 2017, as shown in Figure 2 (boxed in red), it was composed of 3 files, namely, "mcoemcpy.exe, mcutil.dll, Mlog.dat or macafee.res."
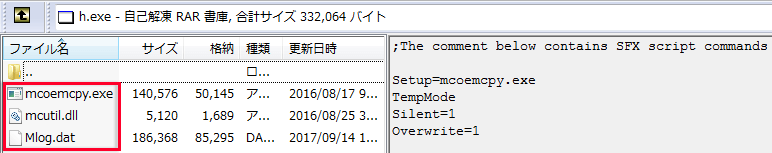
On the other hand, in the PIPX we have seen around April 2016, (boxed in blue dotted lines) it consisted of 3 files, "RasTls.exe, RasTls.dll, RasTls.dll.msc."
2. How Automatic Execution works
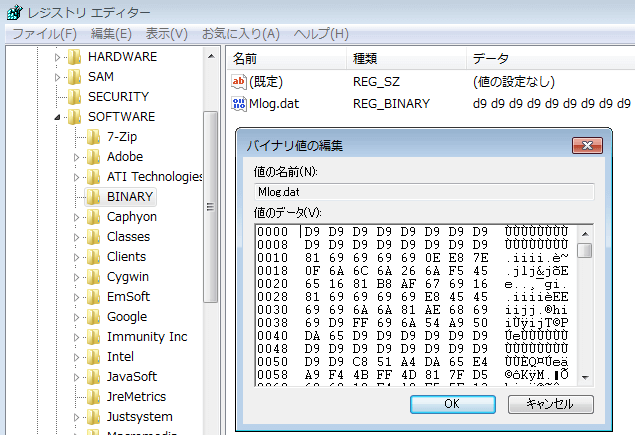
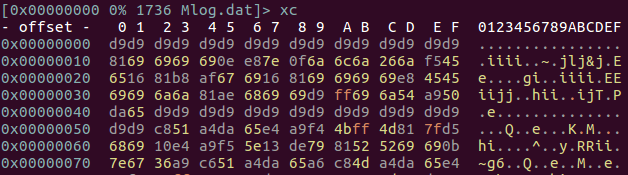
PIPX is executed automatically by a legitimate program in the Service or the Autorun Registry Key (1), after the DLL side-loading is exploited. During this process, the encrypted data is not read as a file, but it is read from the registry value stored in the specific Registry Key (2). As shown in Figure 4, it can be confirmed that the value of the data in the registry and the file data included in the PIPX are the same.
- (1) In the case of Administrator rights, "Service" is used, but in the case of General user rights, the "Registry Key" is used
- (2) HKLM\SOFTWARE\BINARY(In case of Administrator rights) or HKCU\SOFTWARE\BINARY(In case of User rights)
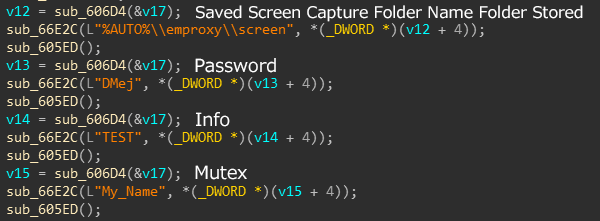
3. Configuration Information
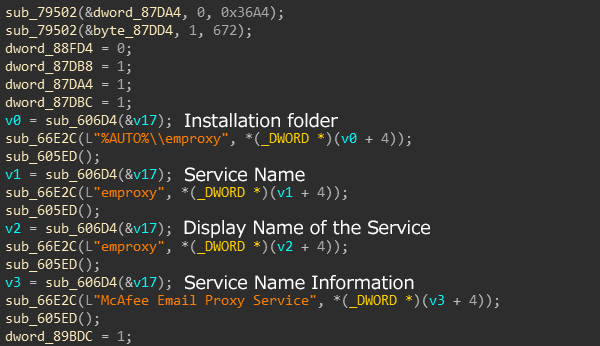
The size of the configuration information is 0x36a4 bytes, as shown in Figure 5, the information is included, PIPX operates based on this information.
PIPX Traffic Destination
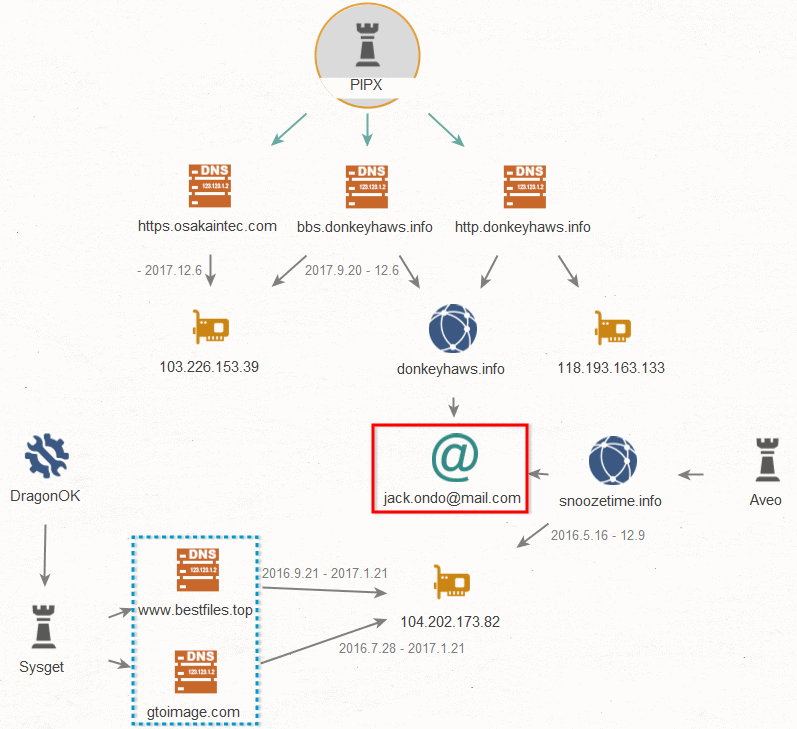
By looking at the traffic destination of the PIPX and based on related factors such as the types of malware and the infrastructure, it is clear that there is a high possibility that this crime is from the APT group called "DragonOK". DragonOK is an attack group that mainly targets manufacturing and high-tech industries in countries such as Japan and Taiwan and is reportedly based in China's Jiangsu province based on a report published by Fireye.*2
Figure 6 shows a Maltego mapping of related elements based on some of the characteristic communication patterns and destinations used by PIPX. You can see "jack[.]ondo[at]mail[.]com" (boxed in red line) as the email address used to register the domain of the C2 server. *3 As reported by Palo Alto Networks, the acquired domain (snoozetime[.]info) using this email is the same domain used by a malware called "Aveo" .
By further investigating the related elements, we can see that the IP address "104.202.173[.]82" associated with these domains is used for the domains (boxed in dotted blue line) almost at the same time. This domain, works as a C2 server and uses a malware called "Sysget" which is one of the malware used by "DragonOK" and we have confirmed that at least in Japan, this malware has been used since around 2014, and it was also used for APT attacks in late Nov 2017. In terms of functions, the "Sysget v4" *4 is considered to be the equivalent of a variant.
DragonOK Expected To Continue Activities Targeting Japan
Although DragonOK activities in Japan were hardly confirmed at the beginning of 2017, around late October, we confirmed some slightly significant movement. From this, since Japan is one of DragonOK's constant targets, we predict that they will actively target Japan on a continuous basis in the future. Our company's threat analysis team would like to continuously investigate this attacker group and will report to the public.
IOC (Indicator Of Compromise)
Hash value
97763d25af878d73d19deabe9ea2d564
29cdae7dc2a7f7376a19e4de91b69c98
58ba2c0ed39d5c874a4933677508f5cc
Traffic Destination
php[.]marbletemps[.]com
bbs[.]donkeyhaws[.]info
http[.]donkeyhaws[.]info
https[.]osakaintec[.]com
206.161.218[.]49
207.226.137[.]207
118.193.163[.]133
103.226.153[.]39