Vulnerability exploitation confirmed on the Web Management Interface of PAN-OS
(CVE-2017-15944)
26 DEC 2017 | Warning Alert
Regarding the vulnerability CVE-2017-15944, it has been confirmed that it can be exploited as announced by Palo Alto Networks in December. If you are using Palo Alto Networks products, please check them as soon as possible.
I'm Shuto Imai, I'm an analyst at JSOC.
On Dec. 14, (local time), it was reported that there is an arbitrary code execution vulnerability on the Palo Alto Networks PAN-OS web management interface.
At the time of writing this report, whether a code is possible to be executed arbitrarily over the internet is yet to be confirmed.
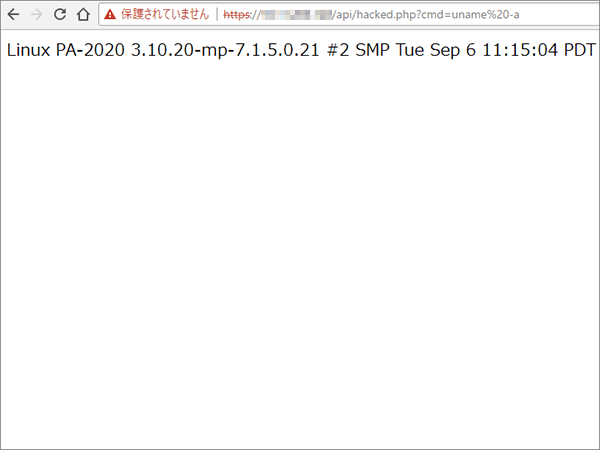
However, based on the results of the verification conducted by JSOC, an authentication bypass on the PAN-OS has been confirmed that arbitrary code is executable.
Although it is necessary to take some steps after authentication bypass, this vulnerability can be easily exploited.
In the environment where PAN - OS runs, execution of OS command, creation of arbitrary file, installation of backdoor etc. with administrator rights may be performed by an attacker.
As of Dec 21st at 9 am (Japan time), there was no attack detected at JSOC, but there is a possibility that an attack that will target this vulnerability may be imminent.
Please confirm immediately that you are not using the vulnerable version of Palo Alto Networks products in your environment.
Affected Versions:
- Previous versions including PAN-OS 6.1.18
- Previous versions including PAN-OS 7.0.18
- Previous versions including PAN-OS 7.1.13
- Previous versions including PAN-OS 8.0.5
Reproduction was confirmed in the following environment:
- PA-2020 on PAN-OS 7.1.5
In the above environment, it was confirmed that execution of OS command with administrator rights is possible.
Countermeasures:
Please update to the following versions:
- PAN-OS 6.1.19 or above
- PAN-OS 7.0.19 or above
- PAN-OS 7.1.14 or above
- PAN-OS 8.0.6 or above
Although we will refrain from citing details of the attack techniques used, we need to take technical steps against the attack methods, but it is relatively easy to implement, and we predict exploit kits will be created.
In an environment where it is impossible to upgrade the version immediately, it is possible to reduce the impact by restricting the IP address accessible to the management interface so that it cannot be accessed from the external network. However, this is an interim measure, the vulnerability will still remain.
We often see access from an internal network to the management interface is allowed in the access restriction policy. However, on this occasion, review the access control and please also consider the establishment of a procedure that upgrading as a permanent counteract can be implemented immediately.