Windows SMB Vulnerability SMBLoris Reproduction Confirmed
10 OCT 2017 | Warning Alert
This is Morihisa reporting on behalf of the Japan Security Operation Center (JSOC®).
As announced at the International Security Conference at the end of July, we have confirmed at our Security Monitoring Center JSOC, the reproduction of the Windows SMB vulnerability called "SMBLoris" which is a vulnerability that comes with the Windows SMB Server, and we have investigated the level of severity of the attack as well as the verification code used for persistent attacks.
In Windows, Server Message Block (SMB) function, which allows transferring files among different machines, is applied. SMB enables applications on the machine to read and write and also to request services from another machine in the network. This function is activated at the initial setup, and once the network is enabled, you can take advantage of its more advanced features.
At the end of July 2017, the manipulation technique of this SMB vulnerability was publicly announced at the International Security Conference. This vulnerability was named "SMBLoris".
The "SMBLoris" reproduction was confirmed on "End-Of-Support" (EOS) products such as Windows Vista and Windows Server products etc. and LAC has announced globally the dangers seen in this vulnerability and we have also verified its range of impact and severity.
- Windows Server 2016
- Windows Vista
- Debian 5
Based on our test environment, we confirmed massive memory consumption occurs in both Windows and Linux and while the server is under attack the entire load increased which seemed to have caused the server to hang up.
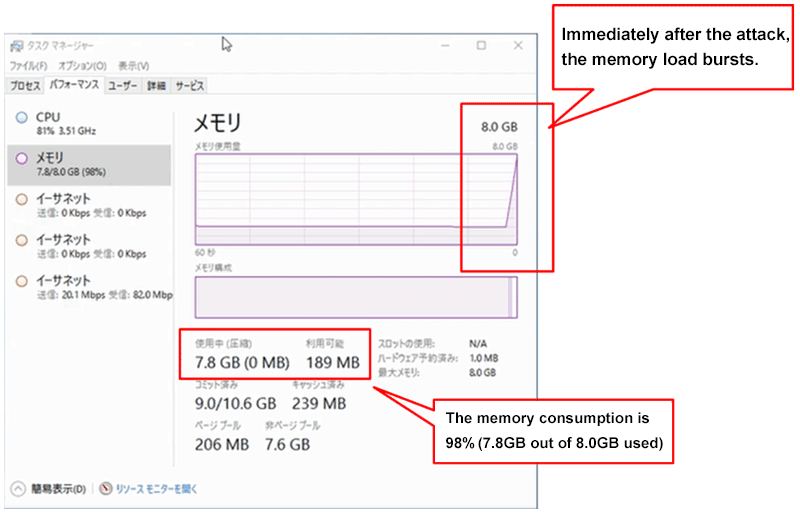
In May this year, SMBLoris has become a hot topic and even now it is regarded as a big issue in Japan, and just like the ransomware WannaCry, it attacks the same port 445 used by SMB.
Preventing Attacks That Use SMBLoris
From the developer company of Windows, Microsoft, up to now there has been no information published regarding this vulnerability and they haven't provided a basic countermeasure to work as a security fix. Therefore, in order to take any countermeasures against this vulnerability, it is necessary to disable communication via SMB.
- Deny connections to port 445 on routers and firewalls to block attacks from the internet.
- In the company's network segment router, deny connections to port 445 on servers that do not provide file sharing functions.
- On the client's firewall function, deny connections to port 445
If the server is using file sharing, by setting to deny connection, it will be impossible to share files. So please consider the business impact.
Has the attack SMBLoris reached the computer you are using?
In order to provide support against the ransomware "WannaCry" LAC has released "Jisin Kun" to assess if the attack can be reachable to the endpoint. Access to "Jisin Kun" from a web browser of the endpoint you would like to check so that you can check any communication from the internet to Port 445.
- Access to LAC's "Jisin Kun" via a web browser.
- After confirming "Term of Use" and "Frequently Asked Questions", tick "I agree to terms" and click "Next".
- On the next screen, tick items you would like to check and click "Next".
- On the next screen, the assessment will start when clicking "Start Diagnosis".