The Relationship Between the Attack Group menuPass and Malwares "Poison Ivy, PlugX, ChChes"
30 AUG 2017 | Warning Alert
It has been reported from JPCERT/CC that from around October 2016, targeted emails disguised as an existing organization or individual are being sent to local organizations.
ChChes - Malware that Communicates with C&C Servers Using Cookie Headers*1
Malware Leveraging PowerSploit*2
It comes as a zip file attached in an email. Once you decompress the executable file disguised as an icon, the malicious file comes out when opened through MS Office Word (hereafter, executable files disguised as icons), or a shortcut link (.lnk) (Figure 1). Having a bot function known as the ChChes, when either of the files is executed, the malware infection begins.
At our Cyber Emergency Center, we have received several inquiries about this targeted mail and while analyzing the malware, we scrutinized the attackers' methods. Among them, I will introduce the relevant features of this malware with IOC (Indicator Of Compromise) by one of the attacker group, known as menuPass (APT 10).
In addition, on Feb 16, 2017 Palo Alto Networks posted on their blog*3 that this attack was a crime committed by menuPass.
About malware that menuPass uses
According to a report published by FireEye on Poison Ivy (PIVY)*4, menuPass, an attack group (campaign name) was targeting defense-related companies in the US and other countries around 2009. After that, around 2011, the target shifted to Japan aiming at universities and government-related establishments in Japan.
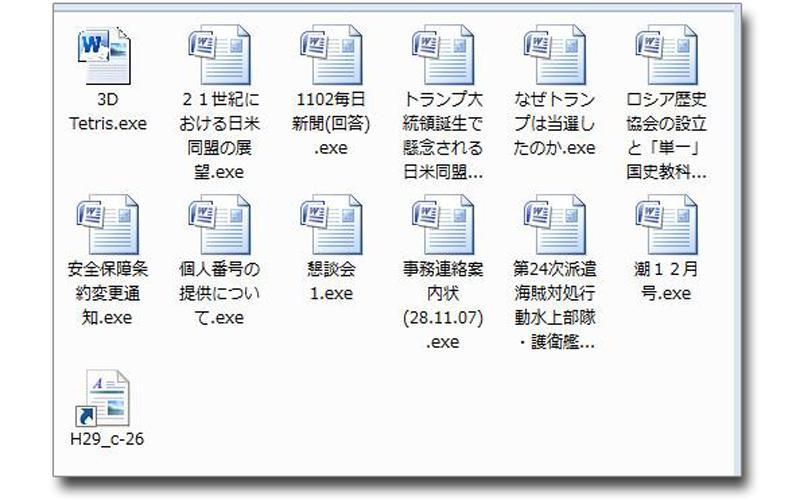
Although the malware used by menuPass was mainly PIVY and PlugX, the new ChChes began to be used around Oct 2016. When we summed up the compile time *5 for all these malwares collected, we can confirm how the attacker group has been changing the malware they used through the years as shown here (Figure 2).
PlugX is a malware used by many attack groups and its features have been improving year by year. Among them, menuPass normally uses the size of configuration at 0x2d58 bytes of PlugX and as one of its features, prefers to use character strings such as "admin#@1", "stone#@1", "flowerdance" as the password in the configuration.
You can see the features of PIVY and ChChes used by menuPass in FireEye's report and also in the JPCERT/CC blog, respectively.
About Executable Files Disguised as Icons
For malware used by menuPass, in the icon resource information we can see its features and we can find out that quite a number of icon information have been set up.
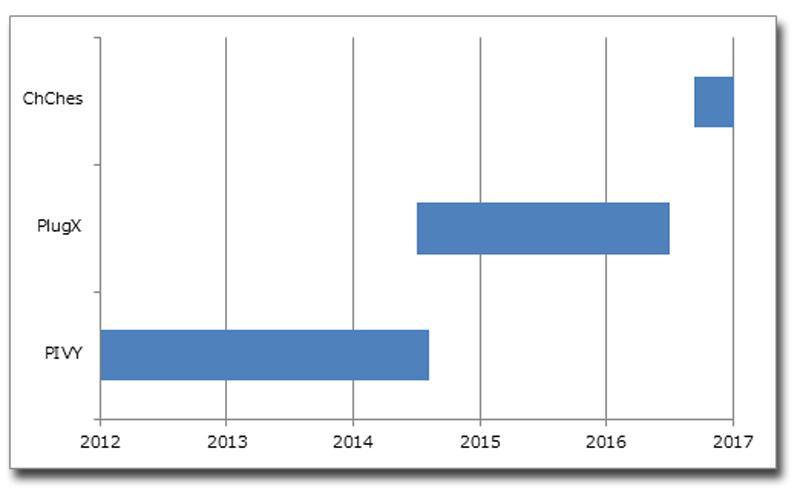
In Figure 3, it shows the comparison of the icon resource information of an executable file disguised as an icon including PlugX and ChChes.
By looking at the resource information of the two executable files, the icon files embedded are similar but the language used to create them is different.
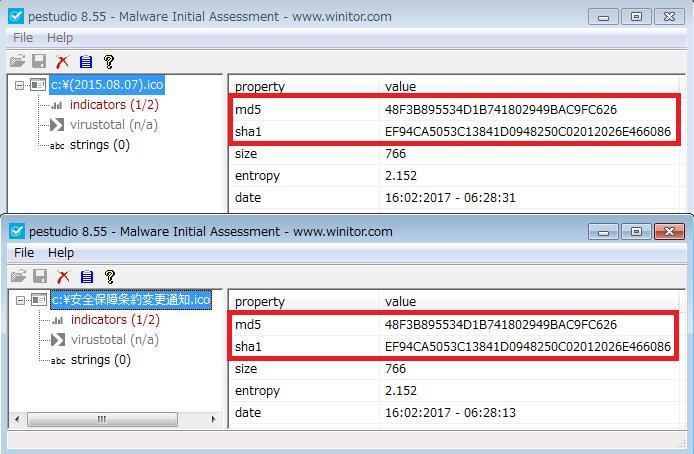
This icon shows it's a Chinese chess piece (Chinese chess).
Although the language used creating the file was different, upon exporting the two icon files and comparing the hash values, we confirmed that they are identical (Figure 4).
From this, the possibility that the PlugX and ChChes were both created by the same malware creator is very high.
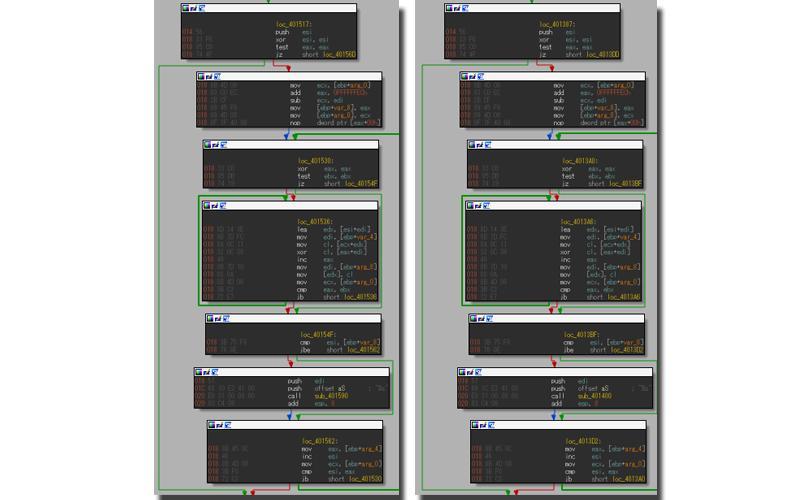
Also, we are able to confirm that the deployment codes for the main body (payload) of PIVY, PlugX and ChChes are similar in many of the executable files disguised as icons.
In Figure 5, by comparing the expanded cases of PlugX and ChChes, even though each of the XOR keys was different it shows that the same codes were implemented. We also confirmed that in some cases they are using RC4 instead of XOR.
About the Command Server Infrastructure
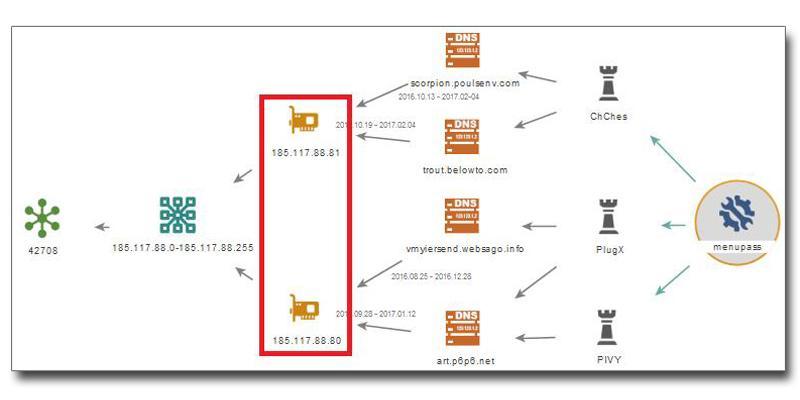
menuPass tends to use several VPS (Virtual Private Servers) to send commands to the command server.
As an example, we confirmed that the traffic destination of PIVY, PlugX, ChChes found in cases with a common IP address was managed by HostZealot (AS42708), a VPS Service Provider in Sweden (Figure 6).
In addition, although we haven't confirmed the other common command servers used by these three malwares, we are quite sure that PIVY and PlugX use more than one common command server.
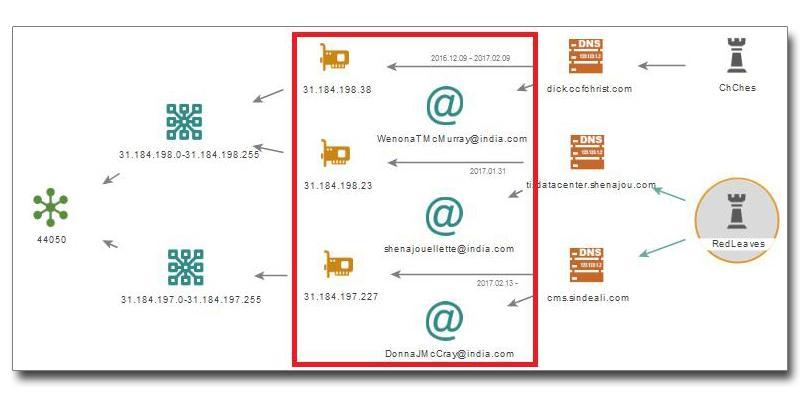
Moreover, there was a new type of malware (RedLeaves*6) that seemed related to the command server infrastructure used by ChChes.
As shown in the boxed section of Figure 7, we can see that the mail address was acquired from india.com and similar character strings are used in the account name. Also, you will notice that the IP addresses are related.
As for the relationship between RedLeaves and menuPass, we have little information on RedLeaves at the moment, but we are thinking of continuing to keep track of trends.
menuPass has been targeting Japan as one of its targets since around 2011, it has been constantly sending attacks and there is a high possibility that it will continue to target Japan.
As a means of infection, targeted mail with ZIP file containing an attached executable file comprises the majority of the cases, however, there are also cases where attacks are exploiting shortcut files, so we expect attacks will come in various forms going forward.
Under such circumstances, our company will continue to investigate this attack group and we would like to provide information to the public.
IOC(Indicator Of Compromised)
PIVY
08a268a4c473f9920b254a6b6fc62548
ca507b0dd178471e9cadf4ca313a67e3
098bfd5c1e7a5cf9f914c09abacb58f9
2685d8eb6009fd7f03956928f08071de
9b17ce7974a0cdd039ca759f3e31e82a
2186f6a75f13f533d05925c6403f9c5a
22b0ac28f22dec098f3d743be4a8164f
a1d0f8895052b60c4d2860556494f233
75569018fc3dcdf9458545ef5d83626b
6f932e38a2a67e8f73606dc30e7a2d7a
2cfdd81233e787045da7244690762c83
22d799e3fe58e5d10341080d370b683e
9dfab49035ee6c6e9b8bb601c63bdac9
578b17334312f81934adfed048ffdafd
a75bea992cef46c1a4ee5146150540aa
9bb609caf50d36e24b152ee467ef3a61
595205651920d06353e9ef9ef8b6e316
e6c596cfa163fe9b8883c7618d594018
de8ed8c6c2f9f83b70361e16d016f15a
224bc8cb1f2e265ccca90657232d8b4d
45f5b2404eefe7672534bcd13466987d
b1dc1fef5bfd49522a41fbfe808fd46f
PlugX
c870ce1cbc120f74059e5f1bb1f76040
13cdd0d9f222a47589c5c71fa3ac2cbe
53c8096033db54e5ec3d5eb9ac080fc4
e85005524e8e6a8612c9d0899bb952d6
2bd698ae474b18cf4748edd99bd6c9e7
5b425dcf90df36706bcdd21438d6d32a
7af04a468de09c519681dcb0bd77030b
9ee006601c5ee9f6f1992ec38fed63f6
25a2bb2eda3c432a4c1ce481d9ceb2e6
94bdc9ded334eceedfa288ffdd03e30f
257b3ed1145c25e3e67f83f61a637034
583ab1678588b754899b9d2c58f20aa2
62898b77bd9e8e286d6bc760f3e28981
a32468828c12657497cddf57190f5700
b18a316b2ce6e099fe7fbf69283cbc5e
d69598758998cf5f677be9312b807938
ef9d8cd06de03bd5f07b01c1cce9761f
d4398f6f7ba070b6cdee7204f6862bd9
667989ffa5e77943f3384e78adf93510
f86c912661dbda535cbab464e79e26be
17b8e6ac3830ad58afe1a70df4319fae
ac725400d9a5fe832dd40a1afb2951f8
0921d7b4bf06276f4f59c85eb240da29
faacabea42afbc6cd5ce684e1bbfb073
19417f7551bc54db6783823325557773
ChChes
75500bb4143a052795ec7d2e61ac3261
1b891bc2e5038615efafabe48920f200
f5744d72c6919f994ff452b0e758ffee
e8f3790cfac1b104965dead841dc20b2
f586edd88023f49bc4f9d84f9fb6bd7d
1d0105cf8e076b33ed499f1dfef9a46b
684888079aaf7ed25e725b55a3695062
d1bab4a30f2889ad392d17573302f097
472b1710794d5c420b9d921c484ca9e8
19610f0d343657f6842d2045e8818f09
ca9644ef0f7ed355a842f6e2d4511546
0c0a39e1cab4fc9896bdf5ef3c96a716
37c89f291dbe880b1f3ac036e6b9c558
07abd6583295061eac2435ae470eff78
23d03ee4bf57de7087055b230dae7c5b
c1cb28327d3364768d1c1e4ce0d9bc07
ac725400d9a5fe832dd40a1afb2951f8
b0649c1f7fb15796805ca983fd8f95a3
8a93859e5f7079d6746832a3a22ff65c
7891f00dcab0e4a2f928422062e94213
3afa9243b3aeb534e02426569d85e517
472b1710794d5c420b9d921c484ca9e8
f03f70d331c6564aec8931f481949188
779dbb88e037a6ecc8ab352961dbb028
c2a07ca21ecad714821df647ada8ecaa
C2
app[.]lehigtapp[.]com
apple[.]cmdnetview[.]com
area[.]wthelpdesk[.]com
art[.]p6p6[.]net
cao[.]p6p6[.]net
dcc[.]jimingroup[.]com
dick[.]ccfchrist[.]com
fiveavmersi[.]websegoo[.]net
gold[.]polopurple[.]com
idpmus[.]hostport9[.]net
img[.]microtoo[.]info
jimin[.]jimindaddy[.]com
kawasaki[.]cloud-maste[.]com
kawasaki[.]unhamj[.]com
kmd[.]crabdance[.]com
last[.]p6p6[.]net
mailj[.]hostport9[.]net
messagea[.]emailfound[.]info
newdata[.]ygto[.]com
news[.]100fanwen[.]com
quick[.]oldbmwy[.]com
sakai[.]unhamj[.]com
sat[.]suayay[.]com
sbuudd[.]webssl9[.]info
scorpion[.]poulsenv[.]com
sdmsg[.]onmypc[.]org
sendmsg[.]jumpingcrab[.]com
smo[.]gadskysun[.]com
stone[.]jumpincrab[.]com
sz[.]thedomais[.]info
trout[.]belowto[.]com
unspa[.]hostport9[.]net
vm[.]vmdnsup[.]org
vmyiersend[.]websago[.]info
zebra[.]wthelpdesk[.]com
*1 ChChes - Malware that Communicates with C&C Servers Using Cookie Headers
*2 Malware Leveraging PowerSploit
*3 menuPass Returns with New Malware and New Attacks Against Japanese Academics and Organizations
*4 [PDF]POISON IVY: Assessing Damage and Extracting Intelligence
*5 Even though compile time can be technically manipulated, it may be considered accurate by comparing the character strings that comes with the campaign ID etc. of the malware.
*6 The malware has a bot function. In the character string contained in the malware the name RedLeaves was attached.