Beware of sensitive data exposed on anonymous FTP servers
13 MAY 2016 | Warning Alert
Original Japanese page is here
Recently in LAC, we have seen several confirmed cases where personal information of both customers and employees have been leaked out unintentionally from a server connected to the Internet.
In recent years, the role of the information management has been questioned severely wherein anyone could access the external or internal information of the organization. If left untreated, this condition could reduce or shut down business operations and may lead to the loss of social credibility, and may also be linked directly to develop into a financial crisis. It is recommended that members of the management layer should refer to the following information and to confirm as soon as possible in your organization that there are no servers with inadequate access management.
When the internal FTP server's internal information status is "public", it can be accessed from the outside without having to enter any password through an anonymous FTP server and files could be exchanged through "file transfer protocol (FTP server). Anonymous FTP server itself is one of the information sharing means that has been in existence since the dawn of the Internet, but in recent years it is becoming obsolete due to other alternative methods.
The information of about 3400 organizations and individuals in the country had become accessible to the public, even though the majority of the information that became accessible to the public did not cause any damage, although there were invoices or quotations that could be considered trade secrets. In addition, they also contained personal information, such as New Year's greeting card destination lists, employee rosters, and e-mail backup data.
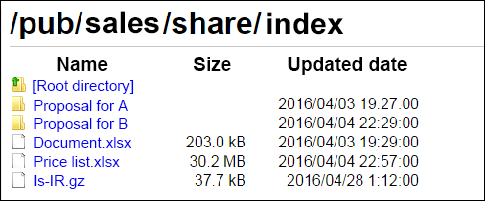
Image of an anonymous FTP server that publishes internal information
It should be noted in most cases, aside from individuals, there are small and medium sized companies that utilize anonymous FTP servers with insufficient management, but as for large enterprises and government agencies, they use anonymous FTP servers for some legitimate reasons.
However, the information that were published unintentionally, among them were many invoices, quotations, addresses, from which any third party can easily browse and confirm the contents, the amounts of transactions, and the names of large companies and well-known organizations.
The lack of setting access permissions was the direct cause of internal information getting published unintentionally. In which case, the following reasons may be considered:
- They did not realize that their servers have been exposed to the public.
- An FTP server that was used in the past is still running even though it is no longer being used.
- An employee working from home has set up an FTP server for personal use and the organization is not aware of the existence of this server.
When internal information gets exposed to the public, there is a possibility that the following problems may arise:
- There is a risk of being liable for information management from customers
- There is a possibility that interaction with customers may be exploited in targeted attacks
- There is a risk that may lead to reputation damage due to inadequate information management after customers' names and information are leaked out
Furthermore, when an anonymous FTP server is in "Write" status, , there is also a risk of the server being used as "file storage" for computer viruses, illegally copied movies, animation, etc.
To prevent information leakage, first, you need to make sure whether an FTP server has been installed and in operation.
Aside from limiting the use of a server machine as a dedicated FTP server, it is necessary to make sure that not just the IT Dept., but it should be noted that individual employees should not be allowed to connect an external hard disk (NAS) to the LAN using a normal PC with Windows functions because in some cases, it can also be installed in the cloud.
Once you find out that there is an FTP server that exists in your organization, or an employee has installed an FTP server privately, confirm the following points and please consider the measures:
- An FTP server should not exist as an anonymous FTP server that anyone from outside can access
- Even if it is intended to be accessed from outside, it has to be set in a state where no one can write to it.→ If it is in such a state, immediately limit the permission not to write to ensure that no suspicious files are uploaded.
- If an FTP server is required for future use
→ If it's necessary for business, set proper access control
→ If it is not necessary, terminate the FTP server. In addition, cut off the communication from outside with a Firewall so that an in-house anonymous FTP server cannot be installed without permission.
FTP server's access management deficiency is the new theme from an old problem.
In 2006, LAC had announced an alert information that the access control rights of the FTP server were insufficient (No password setting, or the ID and the password are the same, etc.) which led to a surge in attacks on FTP servers. Ten years had passed, but it shows the fact that the basics of information security which is access management is still not being thoroughly practiced even until now as unintentional publication of internal information via anonymous FTP server can still be found.
Now it is likely, that any equipment connected to the internet can be accessed from anywhere in world. In January 2016, there was a controversial report that any video screen from network cameras could be set to public viewing unintentionally. In the same fashion, a search service to find any public information via file transfer services (FTP) also exists. Now that any information can easily be found and exposed on the internet, the users, most especially top management personnel, should make sure that appropriate access management is done.
Q&A
Q1: Why did you publish this warning information to the public?
A1: It was published in order to spread awareness. Just like the internet, any person or device is connected to the network and any important information that is not properly managed could be exposed to the public, by using concrete examples, everyone should be made aware of the risks involved.
Q2: What is an "anonymous FTP server "?
A2: When the parties involved try to access the FTP server and instead of using the User ID, an unspecified number of people get connected as "anonymous" from the fact that you enter "anonymously." It's called "anonymous FTP server" in English. Without any form of authentication such as passwords, this setting may permit access to anyone, thus it cannot be considered to fall under "unauthorized access" which is otherwise prohibited by law.
Q3: Were the domestic 3,400 anonymous FTP servers independently investigated by LAC?
A3: About 3,400 FTP servers all over Japan were confirmed to being indexed in the anonymous FTP servers search site. LAC did not have its own FTP server investigated.
Q4: As for the problem server that was exposed to the public, what kind of support did LAC perform?
A4: Regarding the problem server that was obviously exposed to the public, LAC submitted an "Incident Report" for JPCERT / CC.
Q5: Regarding the 3,400 domestic organizations and individuals, were they investigated in detail?
A5: For investigative purposes, it was necessary to analyze in detail the contents of the files, however there were sensitive data not intended for public consumption, therefore investigation by LAC was not performed.
Disclaimer:
Please be self-responsible for the use of the materials in this article.
LAC Co., Ltd. assumes no responsibility for any losses resulting from the use of the information described in this article. When using references to the matters described, please state the original source. LAC is a trademark owned by LAC Co., Ltd., JSOC is a registered trademark of LAC. Other product names listed, the company names and trademarks or registered trademarks are owned by the respective companies.